Infrastructure in an information technology sense is made up of physical hardware such as servers, firewalls, routers, switches and access points, etc., as well as the services they host such as virtualisation technology, web services, LDAP, etc.
Therefore the term Internal Infrastructure is referring to all of those components that lie behind your perimeter firewalls. A security assessment on your internal infrastructure is an assessment that is dedicated to finding security concerns within these networks.
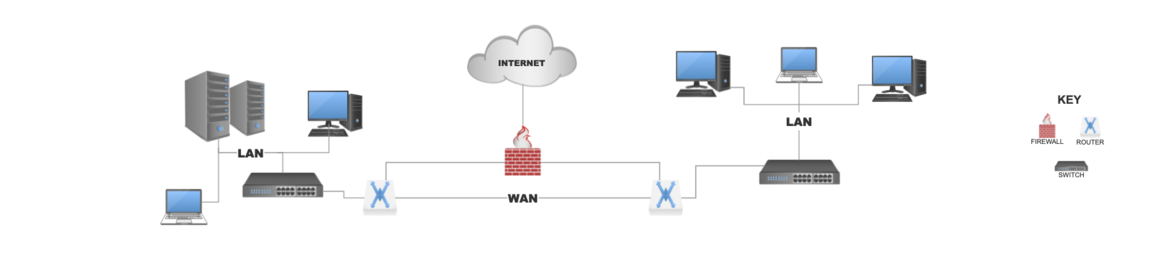
Your internal infrastructure is analogous to the heart and veins of your network. Your physical devices such as switches routers firewalls and servers, supplying the structure to support the blood flow of the system, your data.
This system is made up of various networks described as either a LAN, a local area network, or a WAN, a wide area network. Local area networks (LAN) generally span a relatively small area. Maybe a building or a room in a building, allowing servers, workstations, printers, and people to share resources.
Wide area networks (WAN) generally span geographical areas such as towns, cities, or even countries in some instances. Connecting various LAN networks to one another. In between these various networks you could have switches, routers, and firewalls.
Switches being the aggregator of the systems on the network (servers, printers, workstations), connecting them to one another.
Routers are tasked with directing connections over the WANs or LANs, dictating the most efficient route to take to any given resource.
The firewall is a sort of gatekeeper if you will, sitting between the networks, allowing or denying access to resources across these networks.
INFOSECURITY, https://tinyurl.com/Equifax-WannaCry
Internal Infrastructure assessments look to identify security concerns within this system. Weaknesses could lie in any given part of this system from the workstations to printers, to switches and firewalls, and anything in between.
The weakness could very well be a well-known vulnerability, that with some attention could be resolved quite simply.
Laneden works closely with our clients to understand their drivers and build an appropriate scope of works.
Providing a thorough and independent examination of your corporate infrastructure to identify security vulnerabilities within the software, systems, and network configurations.
We provide an on-site debriefing of the findings explaining how attackers could potentially gain control of your systems and exfiltrate data.
A comprehensive report is written containing an executive summary which gets right to the point of the associated risks identified and is consumable by anyone in the organisation regardless of their technical background.
Along with enough detail to allow you to not only understand the potential attack vectors but also concise and clear guidance on how to either mitigate or remediate the concerns.
It’s important for organizations to focus on building a program instead of deploying a tool.
Vulnerability management has to include asset discovery, prioritization and remediation workflows in order to be effective at reducing risk.”
TRIPWIRE, https://tinyurl.com/unpatched-vulnerabilities-brea
Using a combination of automated and manual testing, our consultants will conduct a thorough assessment of your infrastructure, identifying vulnerabilities that may be exploitable by both authenticated and unauthenticated users across your network.
The use of automated tools and in-depth knowledge of manual testing allows us to accurately and effectively assess your infrastructure, maximising the time available.
Assessments are conducted in line with the current standards and methodologies utilised in the industry, such as those outlined in the Penetration Testing Execution Standard (PTES). Using PTES as guidance, Laneden defines our approach in six phases:
- Pre-engagement
- Intelligence Gathering
- Vulnerability Analysis
- Exploitation
- Post Exploitation
- Reporting
- Our consultants engage with the client to discuss the scope and make certain all is in order prior to the assessment beginning
- Communications at the beginning and end of each assessment day, confirming either the assessment is starting or ending for the day.
- On-going communications from the engaged engineer, highlighting any major issues as they come across them.
- A comprehensive report is provided containing an executive summary which gets right to the point of the associated risks and is consumable by anyone in the organisation regardless of their technical background.
- Clear and concise information describing each issue to hand.
- Technical references will be provided when relevant, allowing you to gather more information on the vulnerability if required.
- Each vulnerability will be put into context and given a risk-based score. Utilising CVSS 3 scoring and relevant context you can get a real picture for each associated risk.
- Simple remediation advice, advising what is required to remediate the relevant vulnerability.
FREQUENTLY ASKED QUESTIONS
PTES is standard designed to provide both businesses and security service providers with a common understanding and framework for performing penetration testing.
Infrastructure penetration testing or vulnerability assessments can provide assurance that systems and security controls have been configured securely with best security practices in mind.
Assure that no common or publicly known vulnerabilities have been identified in your target scope.
If vulnerabilities are identified, they can be remediated before a malicious actor can take advantage of them.
Common vulnerability identification
Potentially avoidance of extra costs and reputation damage due to a breach via a well-known vulnerability.
Provide assurance of effective security controls to regulatory bodies
To assure customers and suppliers, proving you are taking measures to protect their data.
Provide insight into potential risks associated with your network
Provide critical input into your risk management programs
Assessments are priced based on the size of the relevant engagement, how many servers form the scope and any relevant complexities surrounding any scenario-driven requirements. Once requirements and drivers are understood a statement of works measured in days is produced.
The statement of works will describe the total working days required to fulfil the engagement, priced per person day.
Infrastructure assessment scoping is reasonably straight forward, generally, our experienced consultants can produce a statement works simply by using the number of systems in scope.
